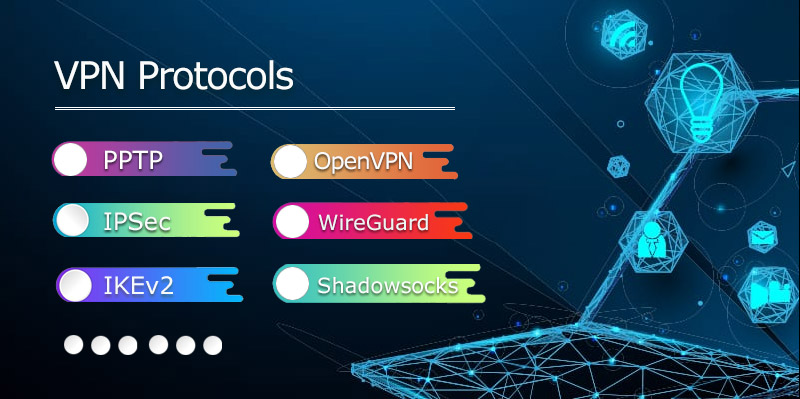
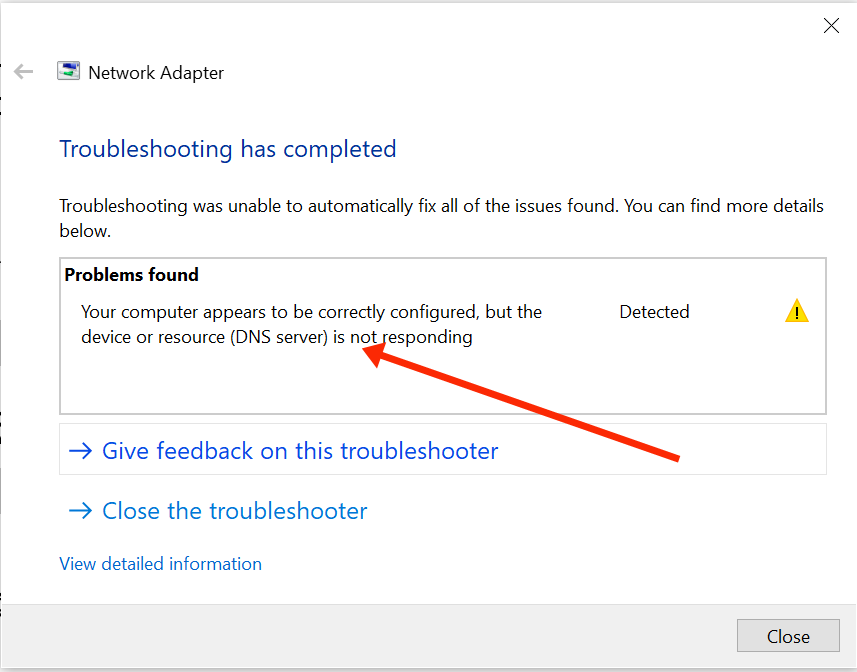
Virtual Private Networks (VPNs) for securing internet connections and safeguarding online privacy have become crucial. While online, using a VPN shields your data from snooping eyes. Yet picking the best VPN is just the beginning. Equally crucial is selecting the VPN protocol that best fits your individual requirements. Your data’s internet transmission and security are governed by a VPN…