WordPress is one of the most widely used content management systems today, making it the most popular platform for creating websites; as a result, it is the most vulnerable to security threats.
This post will go through some of the most frequent reasons why WordPress websites get hacked, as well as practical techniques for securing any WordPress website.
Before we get into it, let’s have a look at the following:
Is WordPress as Secure as a CMS?
WordPress is one of the safest content management systems available today.
Regardless of what others claim, it can survive any known security assault if properly handled.
This is unsurprising given WordPress’s large number of contributors and developer-friendly infrastructure.
Installing WordPress alone (without any third-party plugins or themes) is assured to be secure, as each WordPress version undergoes months of testing and patching before to release.
Other content management systems, such as Joomla, are nowhere near as secure as WordPress.
Try building your own proprietary CMS and you’ll see how difficult and costly it is to make things safe, which WordPress does well as an open-source platform.
Is Your Hosting Provider Always to Blame?
WordPress site owners who have had their websites hacked or infiltrated in any way frequently point the finger at their hosting provider.
This is seldom the case because hosting firms invest hundreds of dollars each year to maintain and safeguard their servers.
They wouldn’t be providing services if they didn’t.
Inadequate security measures and a lack of WordPress administration security understanding lead to website hacking.
Why WordPress Websites Get Hacked And How to Secure them?
Attackers have devised ways to exploit WordPress and obtain access throughout the years, but these may be avoided if proper precautions are followed.
These are the most typical ways WordPress websites get hacked, as well as how to fix them.
i) Using Cracked / Nulled Themes & Plugins
ii) Not updating PHP/ WordPress Version.
iii) Using Outdated Themes & Plugins
iv) Using FTP instead of SFTP or SSH
v) Using a Weak password & default Username
vi) No two-factor authentication
vii) No Activity logs
i) Using Cracked / Nulled Themes & Plugins
Nulled themes/plugins are the most common way for WordPress sites to be hacked; installing a nulled theme/plugin exposes your WordPress site to malicious scripts buried inside it.
Only use and purchase themes/plugins from a marketplace like ThemeForest or directly from a developer’s store to avoid your WordPress website from being hacked.
Only use and purchase themes/plugins from a marketplace like ThemeForest or directly from a developer’s store to avoid your WordPress website from being hacked.
Malicious code and backdoors are frequently found in the nulled WordPress items available for free on the internet, putting not only your website but also your entire server at risk.
Before uploading a WordPress theme or plugin to your WordPress server, do a VirusTotal Scan to make sure it isn’t contaminated with viruses or backdoors.
ii) Not updating PHP / WordPress Version.
Your WordPress websites may be vulnerable to security assaults if you use an older version of PHP or WordPress.
Every online technology improves over time, and new versions are produced; WordPress and PHP are no exception.
Older versions of WordPress, as well as PHP, are now vulnerable to a range of known attacks.
When a significant WordPress and PHP version is released, it is critical to upgrade your website since they are developed with better and enhanced security.
Step 1: Backup Your WordPress Website
Always make a backup of your WordPress website before updating it, just in case something goes wrong.
Some plugins and themes that have not been updated to WordPress’s standards may be broken by new versions, therefore you must have a backup to fall back on.
Some WordPress upgrades may also fail, leaving your entire website in maintenance mode, and having a backup will help you fix such issues quickly.
You may test upgrading the WordPress version of your website in a staging environment before releasing it to your live site.
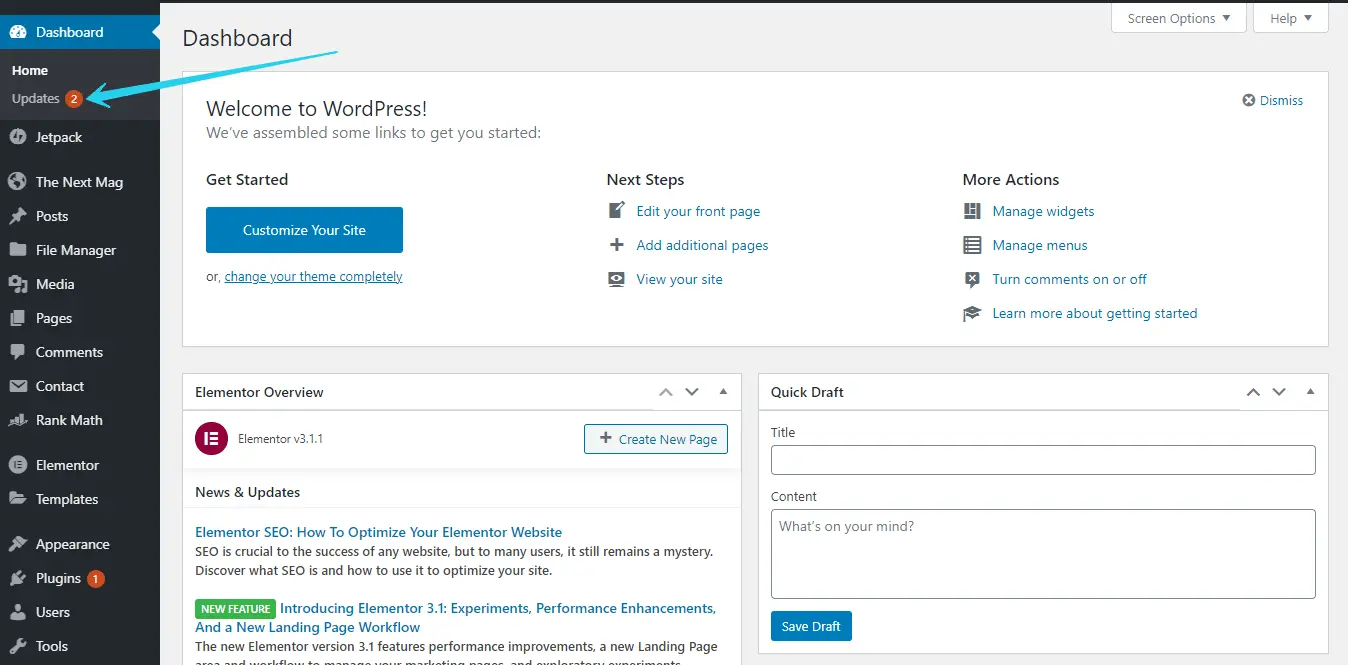
Step 2: Log in to DashBoard & Navigate to Updates Tab
Select the Updates sub-tab right beneath the Dashboard Tab (First Tab on the left navigation bar) in your WordPress Dashboard.
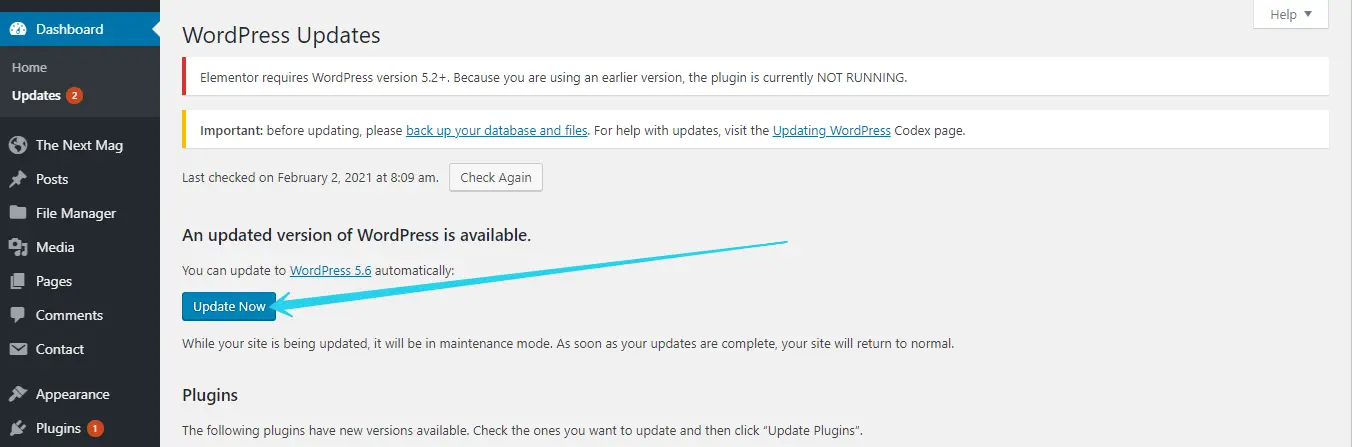
Step 3: Click on the Update Button
You should see your current WordPress version and whether a new version is available after the tab content loaded.
If there is a new version available, an update button will appear, which will start the updating process.
Wait for the procedure to finish after clicking the Update Now button (automatically).
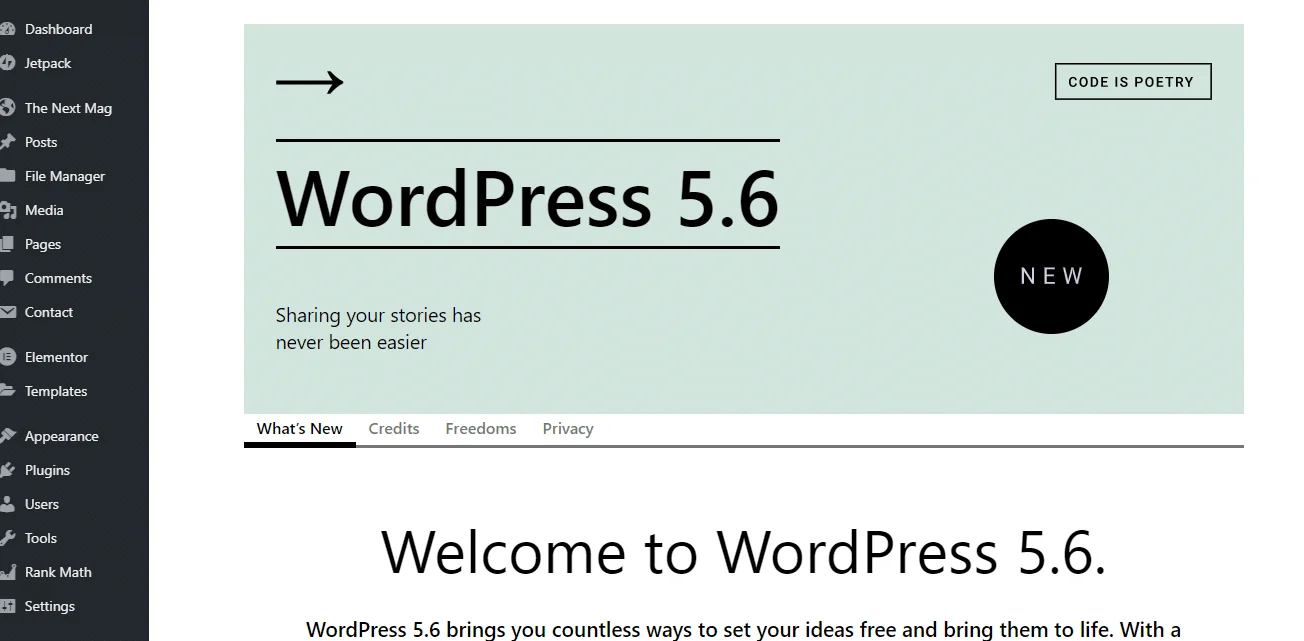
Step 4: Wait For The New Version to be Downloaded & Installed
When the Version update is finished, you should be met with a welcome screen for the version, which lists all of the new features.
To be secure, you should update the WordPress version of your site as often as feasible. They constantly include security patches and new security policies to assist safeguard your WordPress website from unforeseen attacks.
iii) Using Outdated Themes & Plugins
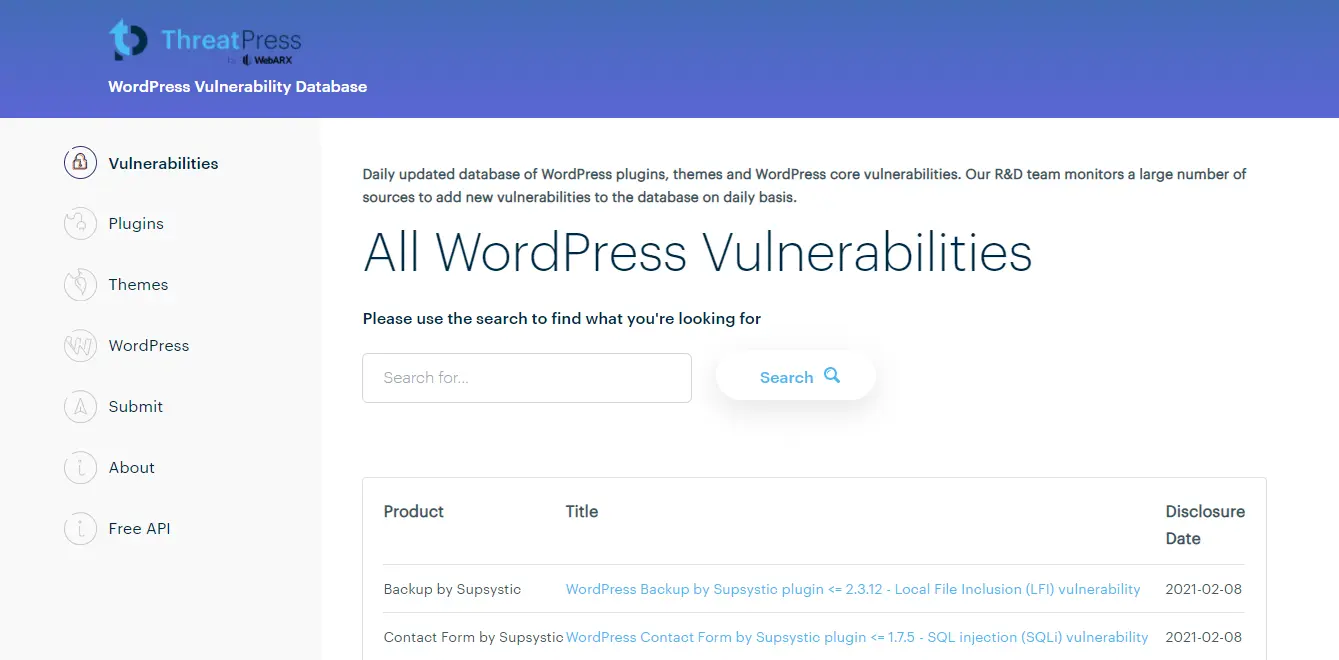
Every day, websites like WPScan and ThreatPress identify new vulnerabilities in WordPress themes and plugins, which the creators of the affected items then repair and distribute to all of their WordPress users.
It’s possible that leaving your themes/plugins obsolete for even a day after an update is released can result in a security issue.
To counteract this security vulnerability, the WordPress team created the plugin auto-update function; activating this option or routinely upgrading all WordPress resources should keep your website safe from numerous cross-site and injection threats.
It’s critical to include running updates as part of your Website administration responsibilities; it’s a common way for hackers to get unauthorised access to WordPress sites.
iv) Using FTP instead of SFTP or SSH
Using a pure FTP connection to connect to your WordPress server is a certain method to get hacked.
Attackers may now easily breach your server using conventional FTP susceptible tactics such as sniffer, spoofing, and brute-forcing.
FTP is insecure because it uses clear-text users and passwords for authentication and does not utilise any encryption.
It’s similar to HTTP, but it’s for file transfers.
Once a hacker obtains access through FTP, they may alter your WordPress files and insert harmful code, granting them access to your WordPress website (backdoors) as well as potentially every other website on the server.
v) Using a Weak password & Default Username
When it comes to gaining access to your WordPress backend, bruteforce assaults are very common.
Using a weak password increases your chances of being hacked by a factor of ten.
Bruteforce technology has evolved over the years with dictionaries of common passwords from millions of hacked websites, making passwords linked to your website (i.e., websitename2021) easier to break.
When you combine a weak password with the default WordPress username (admin), you’re more likely to be hacked.
Your Administrative account’s username should not only be distinctive, but also concealed from prying eyes.
To hide your admin username, create an additional author account for managing and publishing material.
The best answer to this problem is to choose a strong password that includes multiple different symbols, numbers, and words that have nothing to do with you.
When faced with brute-force attacks, a security plugin like WP Limit Login Attempt can help safeguard your site even further.
vi) No two-factor authentication
Two-factor authentication is a security feature that adds an extra step to the login process, making your WordPress website more secure.
Instead of using a login and password, you may use an OTP (one-time password) sent to your email or cellphone number, which entirely blocks anyone attempting to obtain unauthorised access.
Wordfence provides an outstanding Two-factor Authentication solution for WordPress that is simple to set up.
vii) No Activity logs
An activity log is a great tool to keep track of what and who has access to your site; it records all actions performed on the back end of your WordPress website.
From new logins to file tempering to IP tracking, we’ve got you covered.
It maintains track of all of the modifications made to your website. With an activity log, you can be confident that no one other than you and your team has accessed your website.
This is an important feature to WordPress security since it allows you to keep track of when and how attackers obtain access, if they do.
WP Activity Log includes all of the tools you’ll need to set up an effective activity recording system for your WordPress site.
It also has sophisticated features such as triggers, which make detecting breaches much easier.
4 Easy Steps You Can Take to Secure Any WordPress Website
i) Change Your Password
ii) Install WP Login Limit
iii) Enable Auto Update For all plugins
iv) Install & Configure WordFence
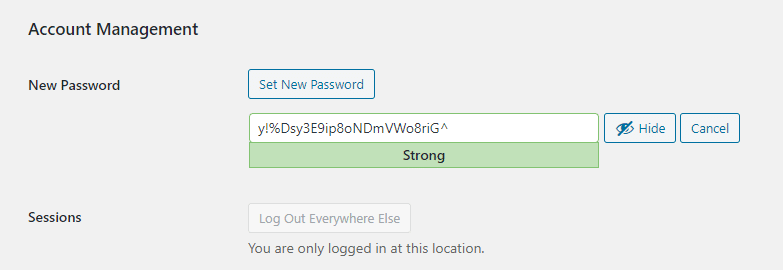
STEP 1: Change Your Password
The first step in securing any WordPress site is to switch from a simple password to something more difficult.
A strong password should be made up of a string of random characters that includes symbols, numbers, and letters.
Make sure your password isn’t too long or too short. You may alternatively utilise WordPress’s default password generation, which adheres to a safe password standard.
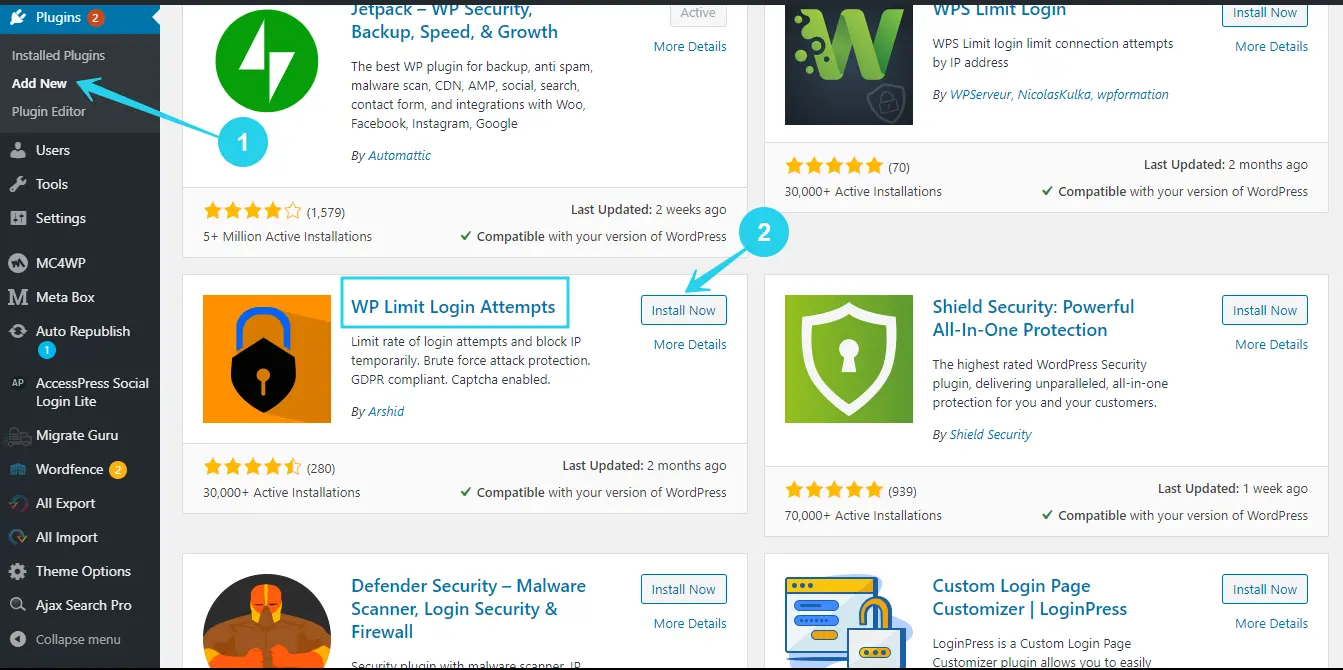
STEP 2: Install WP Login Limit
Still on the subject of login security, restricting login attempts is an excellent approach to put an end to brute-force assaults.
The fewer Login attempts made by an attacker, the more difficult it will be to break through.
Search for WP LIMIT Login Attempt in the Plugins repo on your WordPress dashboard, then install and activate the plugin.
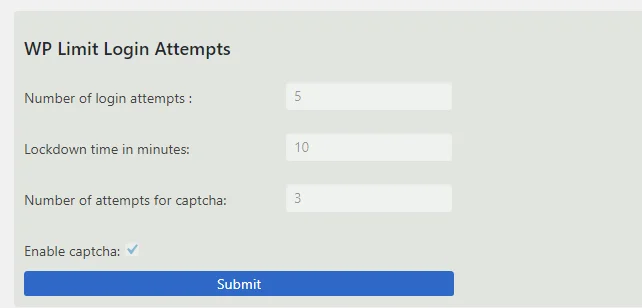
After enabling the plugin, it automatically restricts login attempts on your WordPress site to 5 per IP address, which is enough for an admin but far too few for a brute-force attacker.
STEP 3: Enable Auto Update For all Plugins
This is the most important item on the list, and if you skip it, your website may become insecure.
To begin, ensure that you are using WordPress 5.6, as the auto-update feature is only accessible in this version.
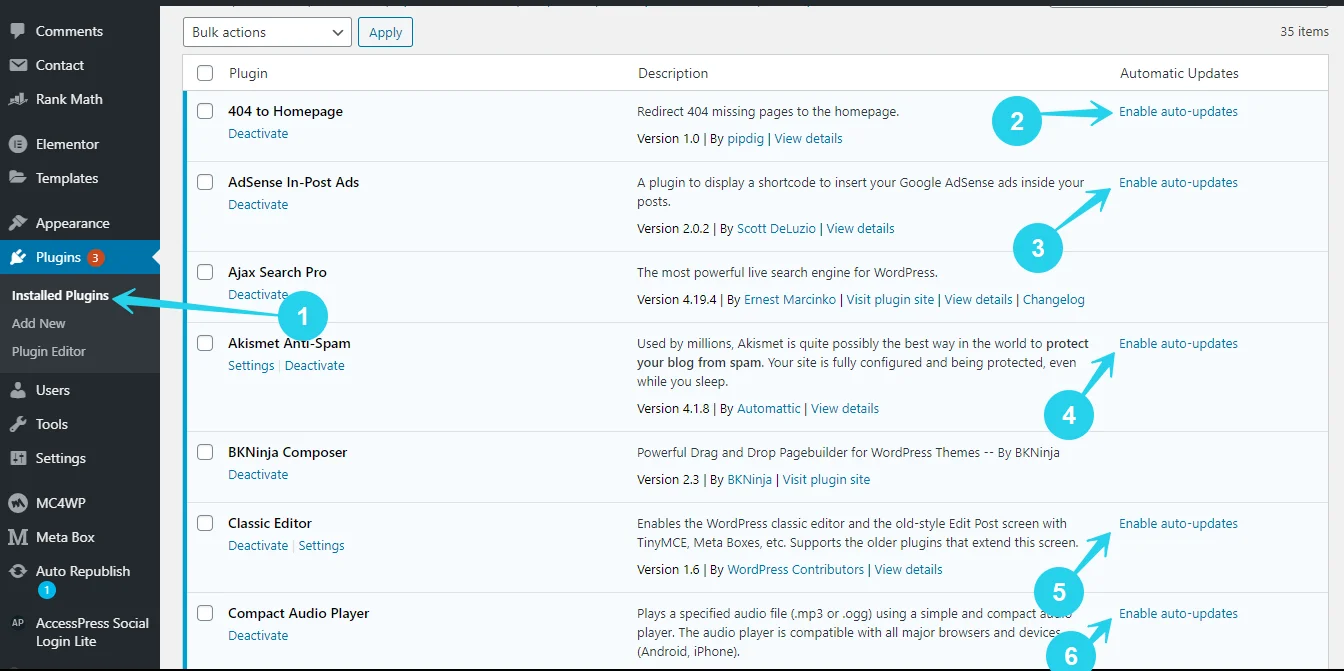
Under the Plugins tab, go to the Installed plugins sub-tab.
On the right side of each plugin, you’ll notice an option to activate or disable auto-update for all listed plugins.
To avoid using outdated plugins with potential vulnerabilities, make sure this is turned on for all plugins.
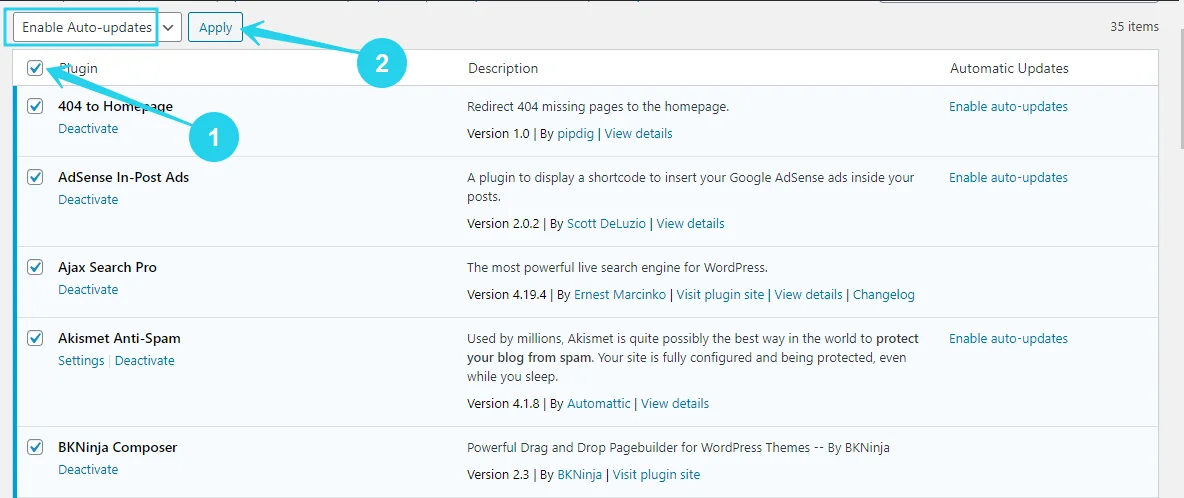
You may also save time by utilising the Bulk Edit option on your plugin page; simply pick all plugins, allow auto-update, and apply.
If you have any Nulled / Cracked plugins on your WordPress site(s), you should delete them right away.
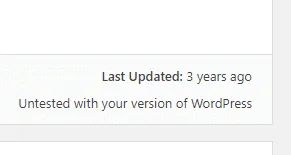
Also, avoid installing plugins that haven’t been updated in over 7-8 months, since they’ve most certainly been abandoned and may include security flaws that hackers might take advantage of.
It’s all about keeping WordPress resources (Plugins & Themes) up to date as often as feasible; this helps maintain WordPress secure.
STEP 4: Install & Configure WordFence
Without a full-fledged security plugin, no WordPress website is completely safe. There are several on the market right now, but none come close to what WordFence provides.
Install the WordFence Security Plugin for this step, which includes a robust WAF (Web Application Firewall) that filters script requests and protects against all types of injection/cross-site threats.
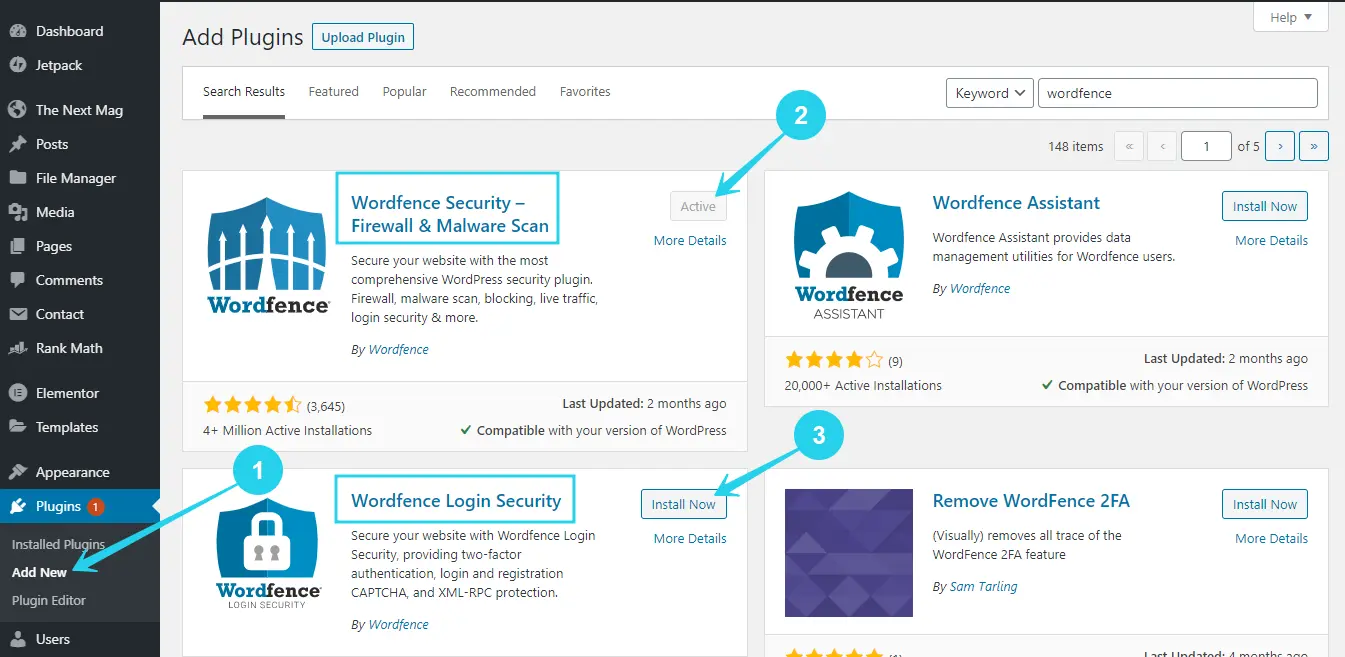
Go to the Plugin repository and look for Wordfence.
Once you’ve found the plugin, activate it by clicking the install button. You may alternatively install WordFence Login Security as a replacement for the two-factor authentication and login limit plugins we recommended in the previous stages, which include these functionality and more.
After activating the WordFence plugin and following the easy setup tutorial, your WordPress website should be safe enough to withstand waves of assaults without being hacked.
Why Do We Recommend WordFence?
WordFence is not only free, but it also comes with a slew of powerful security capabilities that no other plugin can match.
WordFence has a number of features, including: a Web Application Firewall (WAF), WordPress EndPoints Protection, Integrated Malware Scanner, Brute Force Protection (Login Attempt Limiter), Themes/Plugin integrity Checker (Vulnerabilities & Authenticity), Security Threat Check & Notification, File Scanner, Two Factor Authentication, Bot protection (Captcha), IP Blacklisting, And Activity Logging (Monitor Visits & Hack Attempts).
It’s more of a full-featured security package that can quickly apply the majority of all security recommendations on any WordPress website.
WordFence or any full-featured security plugin should be installed as a safety net for WordPress security.
Conclusion
This post has covered some of the most common causes for WordPress sites being hacked, as well as how to keep your WordPress sites safe.
We hope you find this advice helpful in boosting the overall security of your WordPress websites.
You may be confident that attackers would have a hard time breaching your website backend if you take security seriously for all your WordPress websites and follow the guidelines in this tutorial.
We take server security very seriously here at Server Gigabit, and we offer Servers that are designed for WordPress security and speed, as well as a 24/7 support team to assist you if you have any problems.
Today, you can sign up for one of our Web Hosting Plans and never have to worry about server security again while following this guidance to keep your WordPress website safe from hackers.
Please do not hesitate to post a comment below or contact our help staff if you have any issues concerning WordPress security.