The Management Operating System, or MOS, is a collection of practices, meetings, and tools used to structure your process for producing results. A management operating system is in charge of adhering to, carrying out, checking, and acting on a plan to enhance the cycle to gain control and enhance the performance of the patching process. The automatic patch management procedure that helps you to save time and avoid errors is patching, which can be a time-consuming operation.
UNIX literature refers to the person responsible for managing the operating system as the system administrator. Just a few system administrators can be considered an administrator. There are related guides available to assist system administrators with their countless responsibilities.
What is the lifetime of patch management?
Obtaining and testing patches, identifying code changes, testing and deploying patches, adding features, correcting bugs, and closing security gaps are all included in patch management, a subset of system administration. Updates for software and operating systems (OS) are the solutions for programs or products that have security issues.
Patch management is necessary for keeping abreast of newly published patches, determining which unreleased fixes are required for particular software and hardware, testing the patches, confirming their correct installation, and documenting the entire process.
Why is patch management necessary?
Some well-known frameworks and laws, including ISO 27001, PCI DSS, and NIST, recommend implementing patch management.
It’s important to handle patches for the following key reasons:
Security:
Patch management fixes weaknesses in software and applications that are vulnerable to cyberattacks, helping your institution to lower its security risk. The Cybersecurity and Infrastructure Security Agency (CISA) advises utilizing computerized options if they are functional.
A system’s uptime:
Patch management guarantees that your software and apps are kept current and run properly, confirming system uptime.
Compliance:
Institutions are frequently required to maintain a specific level of subordination by regulatory agencies due to the ongoing rise in cyberattacks. A crucial component of maintaining compliance standards is patch management.
Feature upgrades:
Further software bug fixes may be moved under patch management to make room for feature updates. Patches may be required to guarantee that you have the most significant and delinquent derivative offers. In addition to measures, there are benchmarks or KPIs (KPIs). They are adjusted to express the performance level you are aiming for.
What varieties of patches are there?
There are several different types of patches:
1. Software patches
There are designed to address faults or vulnerabilities that have already been discovered after a piece of hardware or software has been terminated.
2. Hotfix:
A hotfix patch is created to fix a particular issue. Unlike standard patches, these hotfixes are created and made available as soon as it is practical to do so in order to minimize the effects of a software problem.
3. A point release,
sometimes known as a dot release, is a brief or relatively short update that is intended to correct bugs or other issues with existing software without introducing new functionality.
4. Maintenance Release:
Incremental updates between service packs or software versions address a number of open problems.
5. Security patches:
A security patch is a modification made to an asset to address a vulnerability’s identified flaw.
6. Service Pack (SP) or Feature Pack (FP):
A software application may get a number of updates, corrections, or feature additions in the form of a single installable patch. They frequently denote numerous significant issues and frequently include all of the patches, hotfixes, management, and security patches released prior to the service pack.
7. Unofficial Patches:
These patches are created by a third party or user group, often as a result of a lack of support from the original software creator, such as when the software company went out of business or after a software derivative reached its designated end-of-life.
8. Monkey Patches or Guerrilla Patches:
A monkey patch often referred to as a guerrilla patch, is an update intended to improve or change the behavior of a software product or plugin locally without changing the source code, much like unapproved patches.
The procedure for patch management
Installing new updates without considering the consequences as soon as they become available for all supports in the company’s products would be a bad strategy. An effective strategy should be followed instead.
Patch management should be carried out using a meticulous, security-focused, and financially advantageous organizational procedure. A centralized patch management server allows the association control over the patch management procedure in addition to automating patch administration. The following are some crucial actions in patch management:
-
-
- Step 1: Create a current:
This step involves observing what resources are there in the ecosystem, whether on a monthly or quarterly basis. You will have a knowledgeable picture of version kinds, existing IP addresses, and their organizational owners and geographical locations through active asset management. - Step 2: Create a plan. While creating a plan is challenging, standardizing your asset inventory makes patching happen faster and more effectively. As new patches are issued, you will need to regularise your assets to a reasonable number in order to speed up your remediation process. This will help the IT teams as well as you.
- Step 3: Create a list of all security measures in Keep an eye on your firewalls, antivirus software, and vulnerability management program. You ought to be aware of what they are guarding, where they are located, and which assets are connected to them.
- Step 4: Compare reported vulnerabilities. With your vulnerability management solution, you may better understand your organization’s security posture and risk by determining which vulnerabilities exist for which assets in your ecosystem.
- Step 1: Create a current:
-
Classify the risk:
You may easily manage whatever assets you believe are crucial to your organization using vulnerability management solutions, and you can then prioritize what needs to be managed as such.
1. Test:
To a representative sample of your lab’s assets, apply the patches. To make sure that the patches won’t cause any problems in the production environment, stress-test the computers before applying the fixes.
2. Put the patches on:
Once you have chosen what to prioritize in order to reduce the environmental risk, start patching. Also, more sophisticated vulnerability management technologies give users the option to automate the laborious steps of the patching procedure.
3. Follow your development:
Verify the success of the patching by reevaluating your assets.
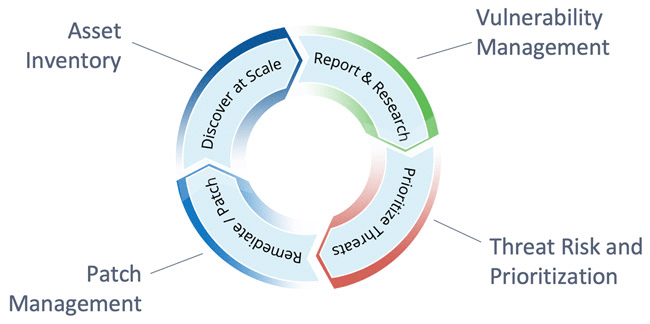
Integrating patch management into measures for vulnerability management:
Any vulnerability management program must have a patch management strategy. But, maintaining a consistent patch management strategy doesn’t always include applying a fix to everything in sight.
Notwithstanding the differences, the terms “patch management” and “vulnerability management” are sometimes used interchangeably. Patch management has a narrow scope, even though vulnerability management and patch management both strive to identify and reduce threats. Businesses should follow vulnerability and patch management best practices holistically to create a thorough security posture. This will give the information required to make wise decisions and increase the efficiency of security measures. System and software security vulnerabilities are continuously prioritized, found, reported, and fixed through vulnerability management.
Vulnerability management is a crucial facet of patch management since it helps to address security flaws. To integrate patch management into the vulnerability management program, the following actions must be taken:
1. Create asset management:
Your ability to reduce risk is only as valuable as your awareness of your surroundings. Let’s say you’re searching for a patch management solution that can provide all the aforementioned security aspects. If so, a variety of solutions are available that provide effective fixes with strong functionality to keep your network patched with the most recent patch releases.
2. Prioritize vulnerabilities.
With restricted time and resources and an ever-changing hazard landscape, it’s ideological to think you can resolve every vulnerability as it appears. Therefore, prioritization is one of the most critical systems of vulnerability management.
3. Remediate vulnerabilities to reduce risk
Recognizing and prioritizing vulnerabilities is necessary, but you’re not lowering risk unless you remediate the problems.
4. Measure the success of your vulnerability management program:
No matter how many flowery characteristics a vulnerability management solution holds, it’s worth the asset if it satisfies your organization’s distinctive demands and adds significance to you and your group.
5. Develop partnerships and support
When something drives faulty, you want to know you have a group of individuals you can depend on to aid troubleshooting.
Vulnerability Patching:
Protecting security in business environments is essential for some reasons, not least the risk of a data security breach or service trouble. Using enterprise software and associated add-ons can yield vulnerabilities that let malicious actors enter your IT environment. Modernizing your systems regularly is significant, and patching vulnerabilities are compulsory to ensure “gaps” are protected. The patching process can sometimes be complicated, as with multiple machines and numerous applications, you must ensure everything is updated. Regardless, patching and editing at inappropriate times can slow down services and applications, eventually affecting your end-user adventure.
Vulnerability patching is stemming your software, applications, and network components for vulnerabilities that could permit a malicious user to access your system and provoke damage. You could uncover your association with a vulnerability when you have a new installation, update, or download.
Vulnerability and Patch Management Process
It’s essential to have a vulnerability and patch management policy surrounding the devices and software you had on your web when they were last patched, a database of available vulnerabilities, a patching schedule, and more. Using a patch management policy across software vendors and the association can keep systems secure.
For Windows, the vulnerability patch management process starts with WSUS and SCCM. WSUS stands for “Windows Server Update Services”, the complimentary vulnerability and patch management tool that arrives with Windows. SCCM is the “System Center Configuration Manager” and is a paid tool. You can also establish Windows systems. Both mechanisms are valuable when handling Windows machines in a large enterprise, especially workstations, and Windows servers.
These instruments are a good beginning for your patching and vulnerability management practice, but their functionality is restricted. Patching tools can produce what WSUS and SCCM propose, which is imperative if you operate many third-party applications or employ a cross of both Windows OS and non-Windows devices on your network. For instance, if your network is moderately available and you have a lot of portable devices connecting seldom, you may be trading with a group of operating systems and machines that ought to be covered.
However, you must maintain a clear patch management plan for your tool. Patching and vulnerability management are continuous processes, so you shouldn’t regularly roll out patches. Deploying and managing patches by procedure across an entire enterprise can generate significant slowdowns for applications and services, eventually affecting end users. Using a tool to assist you schedule and automating patching in a way suited for your enterprise is more beneficial. Once the patch deployment happens, statements on the status of the automated patch management tasks are revised. With an automated Patch Management solution, each enterprise is provided to update its endpoints with the most delinquent patches irrespective of what OS they run and where they are discovered.
Vulnerability and Patch Management Software:
The right patch management software creates all the difference for a thriving vulnerability and patch management process. As mentioned, WSUS is already a feature of Windows systems, and you can also spend for Microsft SCCM. Yet, in multiple issues, you need to look at third-party tools to sustain critical patches for the systems you already own through Windows. How to pick the right patch management software? How do you understand which patch management software is most profitable for your organization? The request differs from business to business. However, there are common periodic characteristics that most organizations peek for in patch management software
A suitable prospect to examine is SolarWinds Patch Manager, which can be exploited for patching servers, workstations, and applications. It also combines well with Microsoft SCCM and WSUS, so you can utilize it to sustain any tools you are operating. Patch Management software supplies a forceful patch management plan, with patch management tools to help you notice which servers and workstations must be patched. In addition, it contains characteristics to help you build deploy patches or patch deployment packages, such as targeting a respective operating system or containing devices exclusively within a specific IP range.