

Log files provide valuable insights into the operation of systems, recording events and messages that can be used to identify and troubleshoot issues. This guide delves into the analysis of log files in both Windows and Linux environments.
Log File Structure in Linux
The location of log files varies across Linux distributions. However, a common location for system logs is the /var/log directory. Apache and Nginx web servers typically store their log files in this directory as well. The specific log file structure may differ between distributions, but some common examples include:
-
/var/log/auth.log: Records authentication attempts, including successful and failed logins. -
/var/log/messages: Contains general system information and startup logs. -
/var/log/dmesg: Captures kernel ring buffer messages, providing insights into system initialization, kernel module loading, and hardware-related events. -
/var/log/syslog: A central log file that receives messages from various system processes and services.
Log Analysis via Systemd
Systemd is the default init system for most Linux distributions. It provides a powerful logging mechanism called the Journal, which stores log entries for all Systemd units. The journalctl command is used to access and analyze Journal entries. To list all active Systemd units, use the following command:
systemctl list-units
To view the log entries for a specific unit, use the -u option followed by the unit name. For instance, to view the Apache web server logs:
journalctl -u httpd
The -since and -until options can be used to filter log entries based on time. For example, to view Apache logs between November 1, 2016, at 8:00 PM and November 3, 2016, at 8:00 PM:
journalctl -u httpd -since “2016-11-01 20:00:00” –until “2016-11-03 20:00:00”
To monitor log entries in real time, use the -f option:
journalctl -u httpd -f
Log Analysis in Windows Event Viewer
Windows Event Viewer is a tool for viewing and managing log files in Windows systems. It provides a hierarchical view of logs, categorized by event type and source. The most important entries for troubleshooting and monitoring include:
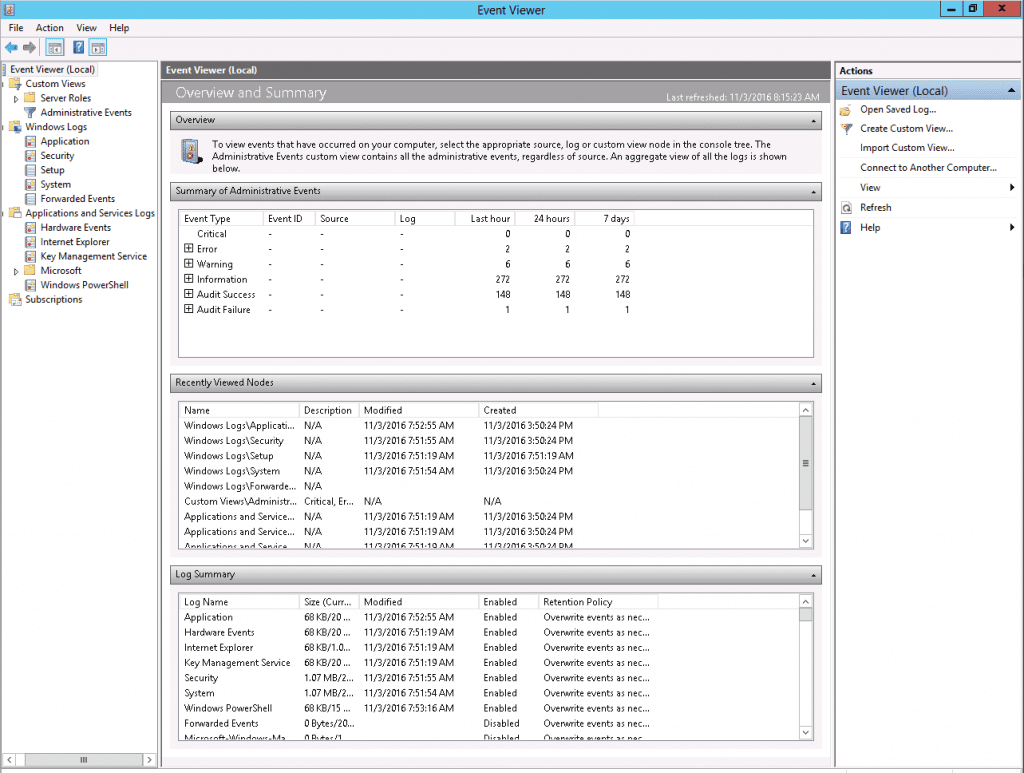

-
Application: Logs events from locally installed applications.
-
Security: Records successful and failed login attempts, as well as security-related events.
-
System: Captures internal events and errors related to the operating system.
-
Custom Views: Provides specialized views for specific server roles, such as Remote Desktop Services.
-
Hardware Events: Logs events related to hardware devices and potential hardware issues.
-
Summary of Administrative Events: Offers a comprehensive overview of the system’s administrative events and potential issues.
Additional Tips for Log Analysis
When analyzing logs, it is important to consider the following factors:
- The purpose of the analysis: What are you trying to learn from the logs?
- The timeframe: What period of time are you interested in?
- The keywords: What specific information are you looking for?
- The tools: What tools are you using to analyze the logs?
Conclusion
Log file analysis is a crucial aspect of system administration and troubleshooting. By understanding the log file structure and utilizing tools like journalctl in Linux and Event Viewer in Windows, system administrators can effectively identify and resolve system issues, improve performance, and maintain system security.
